고정 헤더 영역
상세 컨텐츠
본문
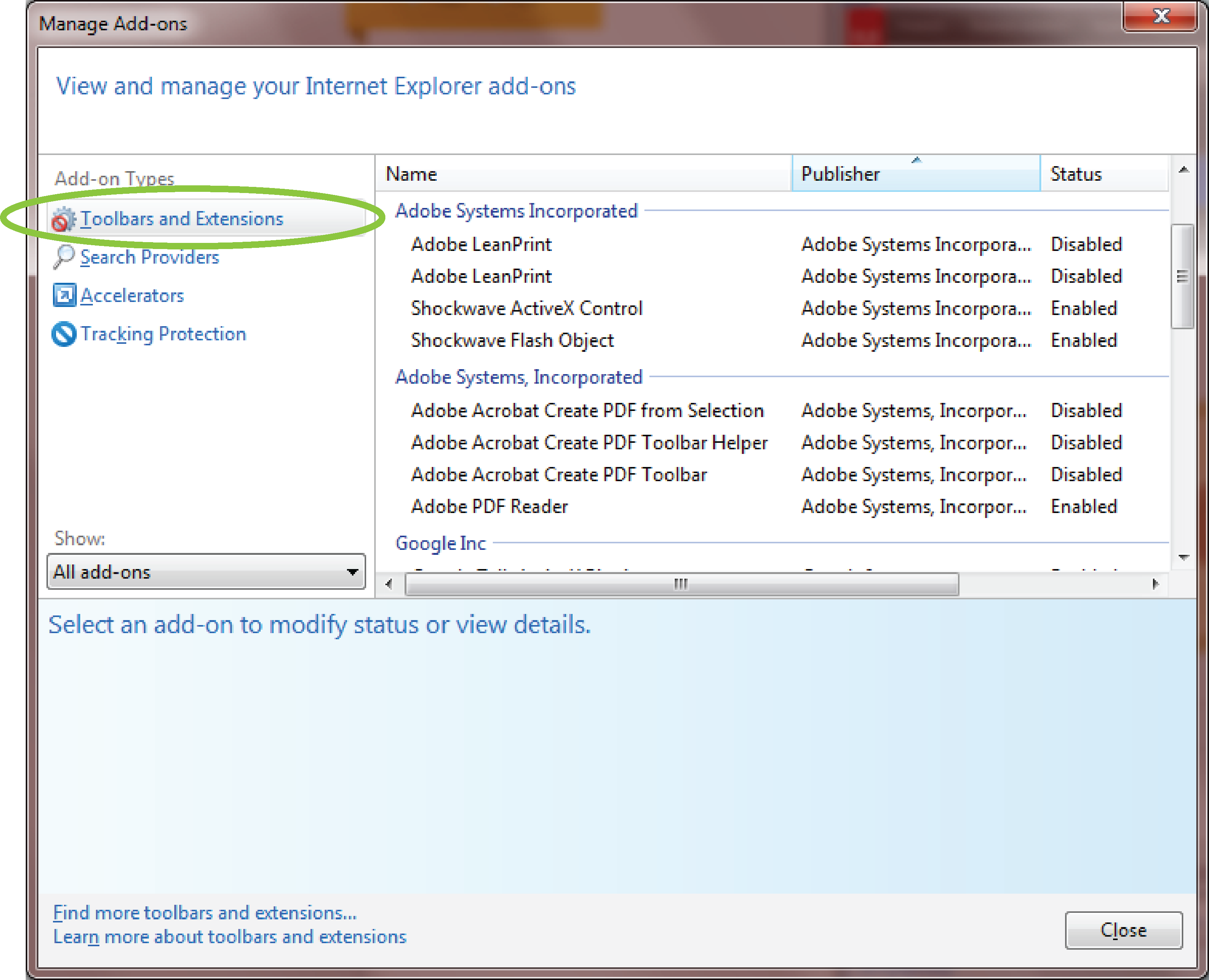
Internet Explorer Restricted This Webpage From Running Scripts On Activex Controls
ActiveX technology was developed by Microsoft for Internet Explorer. ActiveX controls allow developers to encapsulate functionality such as displaying animation, which can then be embedded into other applications. Applications like Microsoft Office also use ActiveX controls to build their feature-set. Programmers can grant ActiveX controls a high level of access to a computer's resources, which makes them powerful but also potentially dangerous.The main problem is that ActiveX security relies entirely on human judgment. Although ActiveX controls are digitally signed, each individual user must decide which ones to install and run. The certificate can prevent scripts from being distributed anonymously or being tampered with, but it cannot ensure how safe the code actually is.
Even though the ActiveX Opt-In feature (introduced with Internet Explorer 7) warns the user if a webpage wants to run a disabled control, it's still up to the user to decide whether to enable it.Signed software can actually give users a false sense of security, and signed ActiveX controls are commonly used by hackers to install malware and spyware from infected or malicious websites. The component's end-user license agreement (EULA) is often incredibly long, but the agreement usually explains what the software is going to do.
.gif)

Therefore, their certificates tend not to get revoked.The only way to avoid malicious ActiveX controls is to do what you have done and refuse all requests to install them. Unfortunately, blocking ActiveX controls completely isn't really an option; if you're using programs such as Word or Excel then you will be using ActiveX components. Also, there are a lot of perfectly legitimate websites that use the controls to make their site more dynamic, interactive and useful. Microsoft's site, for example, makes extensive use of ActiveX components. In fact, the license check made to validate your copy of Windows Vista when you download a patch or utility from Microsoft uses ActiveX controls.Thankfully, IE and ActiveX security risks have declined since the mid-90s when they both first appeared. IE 8 introduces further security controls through its Data Execution Prevention feature, which keeps code from executing from a non-executable memory region. It also performs a check referred to as Per-Site ActiveX, a defense mechanism that restricts ActiveX controls to specific domains, preventing malicious repurposing of controls.
ActiveX vendors can also now block a compromised control using a killbit update package.As to whether you need the Java Runtime Environment (JRE), it's required only if you need to run Java applications. JRE consists of the Java Virtual Machine, core classes and supporting files that provide the minimum requirements for running a Java application. Java security relies on software technology to run applications within a security sandbox. In the past, there have been some security issues with the sandbox. Originally, Java applets couldn't access a computer's local drive as the sandbox was very restrictive. Certain types of programs, such as editors, need file access to be of any use, so some Java-enabled products now use digital signatures to work around this problem. Still, like ActiveX, there's no guarantee that they're not malicious.ActiveX and Java both introduce security risks.
If you allow them on your computer, it's important to keep your OS and applications up to date with the latest version and security patches; always think carefully before accepting a digitally signed program and never surf the Web on a computer that contains highly sensitive information.Load MoreRelated Q&A fromExplore the differences between symmetric vs. Asymmetric encryption algorithms, including common uses and examples of both, as well as their pros and.WhatsApp vulnerabilities can enable hackers to bypass end-to-end encryption and spoof messages.
Expert Michael Cobb explains how these attacks work.Disabling Google location tracking involves more than turning off Location History. Learn how to manage your account settings to stop tracking.Have a question for an expert?Please add a title for your questionGet answers from a TechTarget expert on whatever's puzzling you. Add a title You will be able to add details on the next page.




